Please submit the following details to download this asset.
Please submit the following details to download this asset.
Modelling Application Building Blocks in the Digital Transformation Journey
|
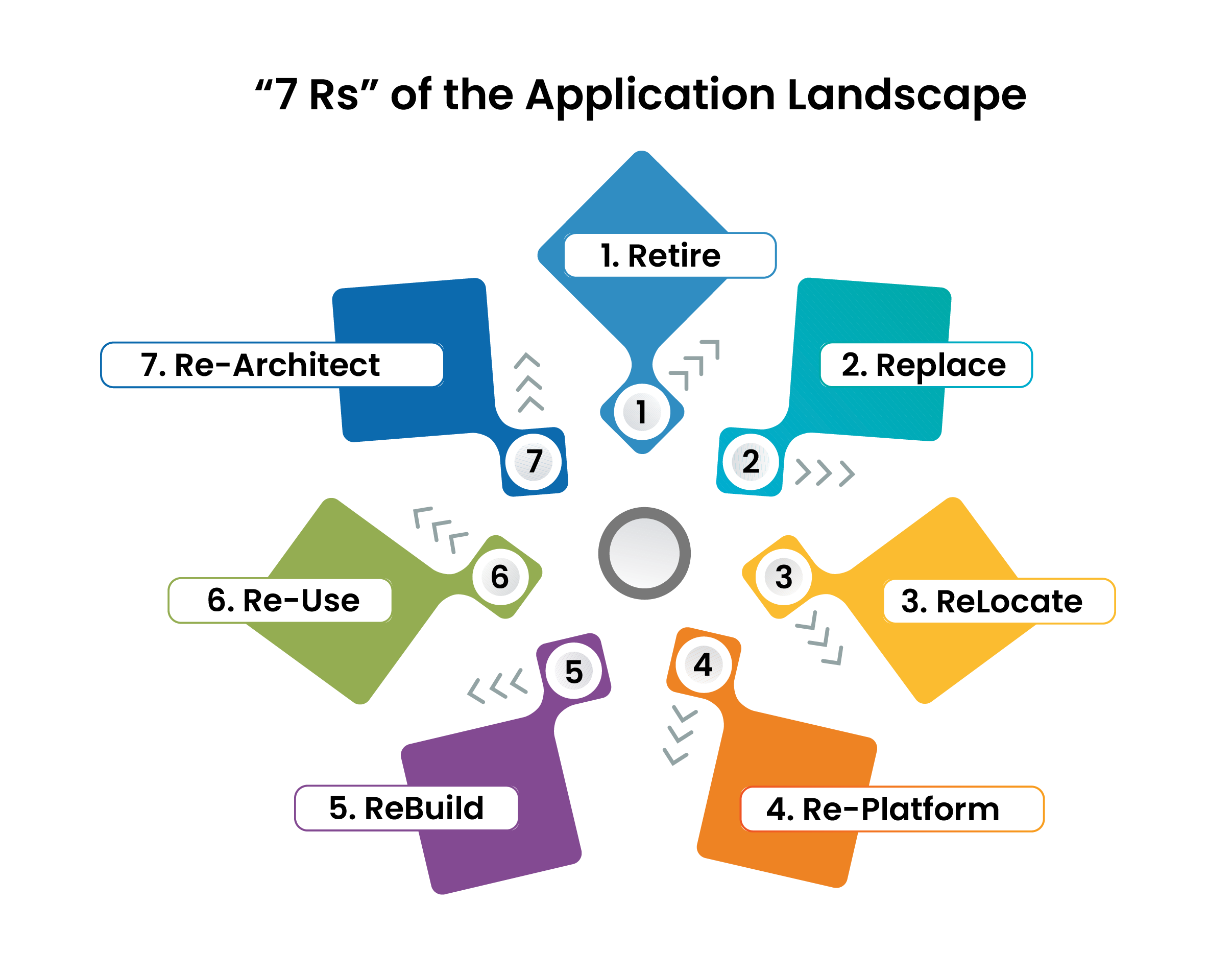
Enterprises today rely on application portfolios to define business strategies and to address line of business demands in a fast-paced digital world. Each application needs to be critically evaluated in the overall scheme of the enterprise digital landscape and this would be the number one priority for CIOs. With a sharp focus on ensuring business impact with every application roll-out, enterprises need to follow the 7Rs of application landscape - Re-host, Re-platform, Re-factor, Re-architect, Re-purchase, Retire, and Retain. Application developers often need to take cognizance of the facts that lead to limitations in the integration, enhancement and performance of individual apps and may turn applications into a liability rather than a digital asset. Be it a new application or a refactored one, it becomes imperative to fully understand the reasons which resulted in its limitations to scale, and its inability to fit into the overall app ecosystem. Thus, it is crucial to understand the various dimensions of the enterprise applications and solidify the Application Building Blocks in the Digital Transformation Journey. |
|
|
Why should you consider different dimensions before building an enterprise application? Business leaders who commission and sponsor application development take keen interest on timeliness of the project and its ROI. These can be measured by active usage of the app by business users and by recording key performance metrics. In today’s fast paced business world where technology requirements are constantly evolving, chasing a moving target is often quite challenging. Hence, without proper provisions to ensure scale and right features, many applications are scrapped mid-way, repurposed, or fall short of expectations resulting in low adoption. To strengthen the building blocks of application development and ensure their success in an enterprise digital transformation journey, technology leaders need to deliberate on a few key considerations. These would essentially provide insights along the entire app development journey right from conceptualization to enterprise roll out. These insights would help stakeholders make the right choices from an early stage of the application development process. Over the course of time, this will ensure better adherence to budget, avoidance of rework, and accuracy of schedules. In turn, these will help create flexible, scalable, and resilient apps. Let’s dive deep to understand each of the dimensions better. |
|
|
Purpose and Build Decision For informed decisions around identifying personas, application types, supporting devices, intuitive user interface, and other peripheral requirements, it’s important to gain insights on application stakeholders, their roles, technology skill maturity, user density by geo location, preferred operating channels, end objective, and time-to-production. Ideally, new applications emerge when the OTS (off the shelf) applications are inadequate to meet the current needs. However, when millions of applications are already catering to diverse requirements, it’s logical to first find any existing applications which can closely meet the needs and fit into the bill, in terms of ownership (CAPEX) and ongoing maintenance (OPEX). |
|
|
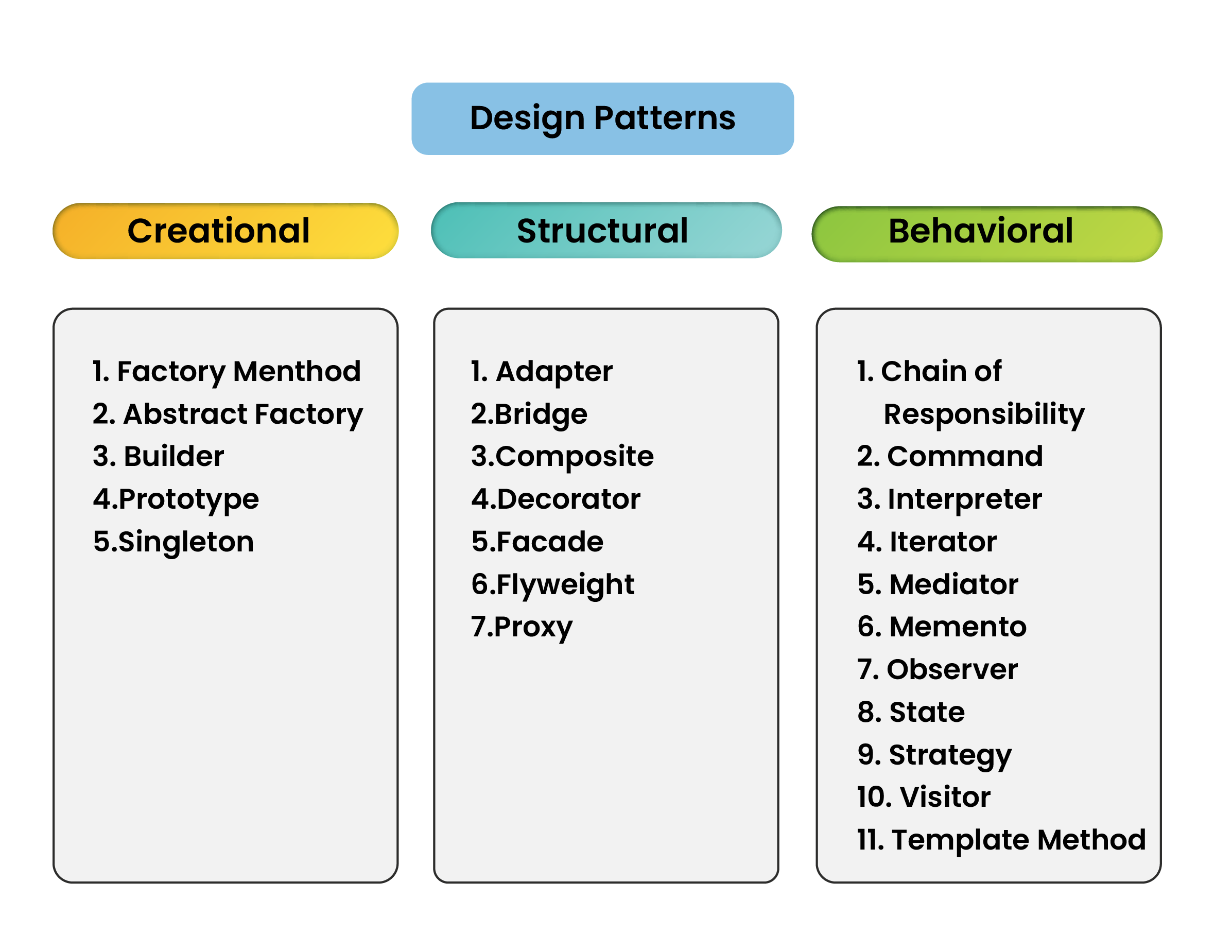
Application Architecture Design Patterns To ensure clear segregation of visualizing, processing, and data management tasks, it’s advisable to use popular architecture design patterns like MVC, MVP and MVVM. Component positioning within these design patterns help to define flow entry, flow control, data binding, and component visibility. Each pattern is also evaluated for compatibility, modularity, modifiability, and maintainability. During the application development, alongside above patterns, software design patterns (3 types, 23 in total) provide illustrations and help to address some of the most common scenarios. |
 |
|
Technology Framework – Frontend When the same application is positioned for multiple channels like web and mobile, there is a trade off in terms of user experience, responsiveness, and native features. In the journey from Responsive Web apps / Progressive Web apps (PWA) towards Hybrid apps, Cross platform apps, and Native device apps (like iOS and android), the reusability of code reduces while the flexibility and robustness enhances. Popular frameworks to address these types of situations are RWA / PWA (like React, Angular, Ionic, and more), Hybrid and Cross platform (React Native, Ionic, Xamarin, Flutter, Sencha and more) and Web (JSP/j2ee, ASP/.NET, HTML5, PHP and more) with few frameworks offering more than one solution. |
|
|
Technology Framework – Backend Backend applications provide data access interfaces (APIs) alongside enabling workflows, accessibility, and integration flows. Within each popular technology stacks, there are frameworks which provide functionality launchpad with configuration options. Some of the API stacks to framework combinations are Spring Boot (Java),Express (Node), Django/Flask (Python), Laravel/ Symphony (PHP) and Web API (ASP.NET). Technologies and frameworks are chosen based on the inhouse and market skills availability, demand & supply, economy, learning curve, and versatility. |
|
|
Developer Setup It's a common practice to centralize the development repository, with most development teams managing their code artifacts on Git platforms like GitHub, Gitlab, BitLocker, or CVS and in a few cases on on-premises servers. Development can be done locally or on virtual machine, VM container, hosted container, or development service platform to carry out typical repository actions. The advantage of cloud platform is to spin a new environment using AMIs / CFT, RMAs or by using base container images which serves as the boilerplate. |
|
|
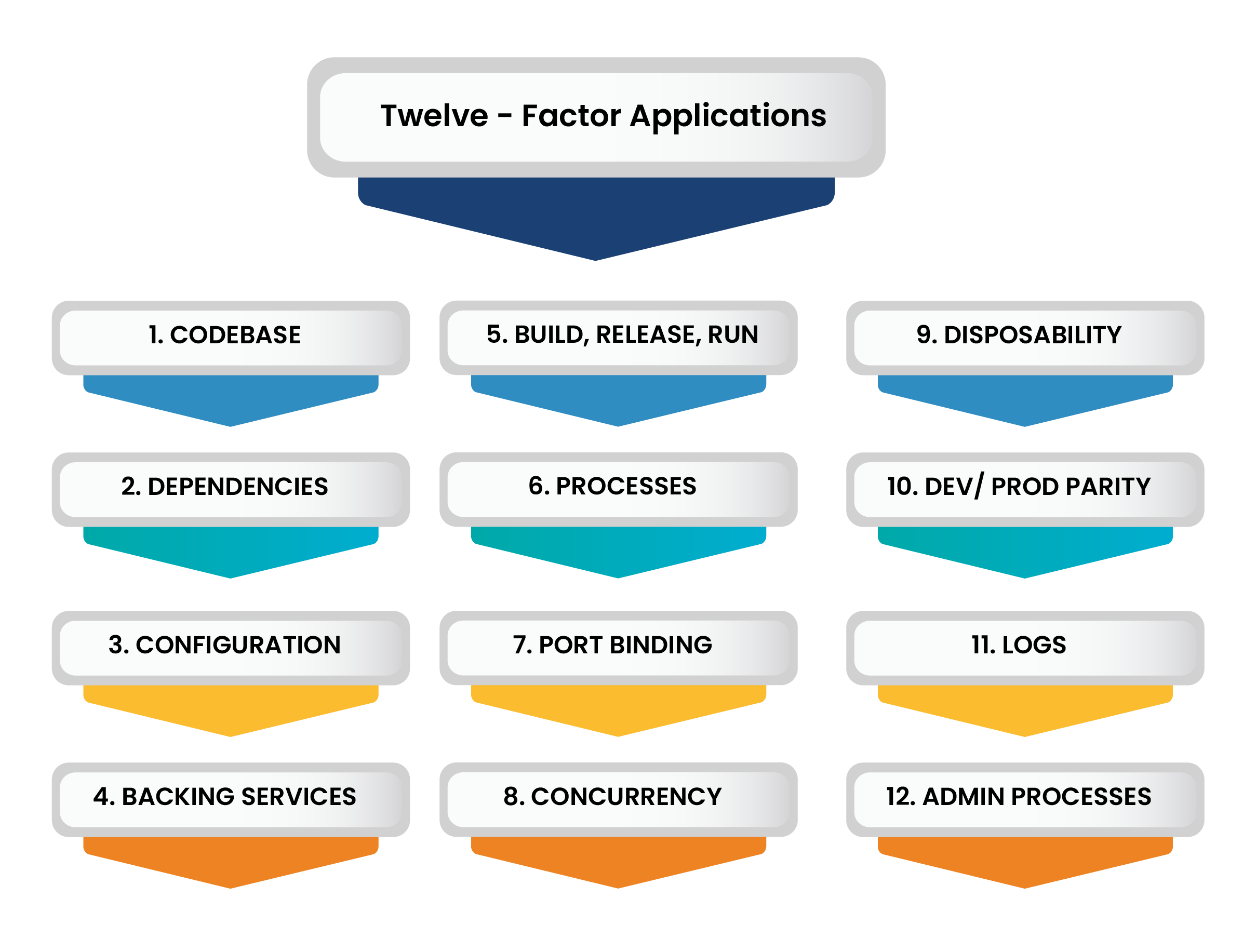
Externalize Dependencies At times, a well-tested module on one developer or server machine doesn’t function on another. When applications pass through environments like development, testing, staging and production, they need some configuration changes. Typical variables are environment specific hardware, dependencies, references, integrations, interfaces, loggers, network, permissions, credentials, etc., which are ideally built once and deployed anywhere. Externalizing dependencies from the environment addresses such challenges which are recommended in the 12-factor app. |
 |
|
Accessibility View and Data are the two aspects of the application accessibility. Some of the commonly used techniques for ensuring accessibility include RBAC (Role Based Access Control), ABAC (Attribute Based Access Control) or Hybrid approach which combines the best of both. At times, too many roles in case of RBAC and too many rules in case of ABAC limits the usability of a single technique. Hence, for large and complex applications, a hybrid approach combining the RBAC and ABAC functionality helps to scale the solution. |
|
|
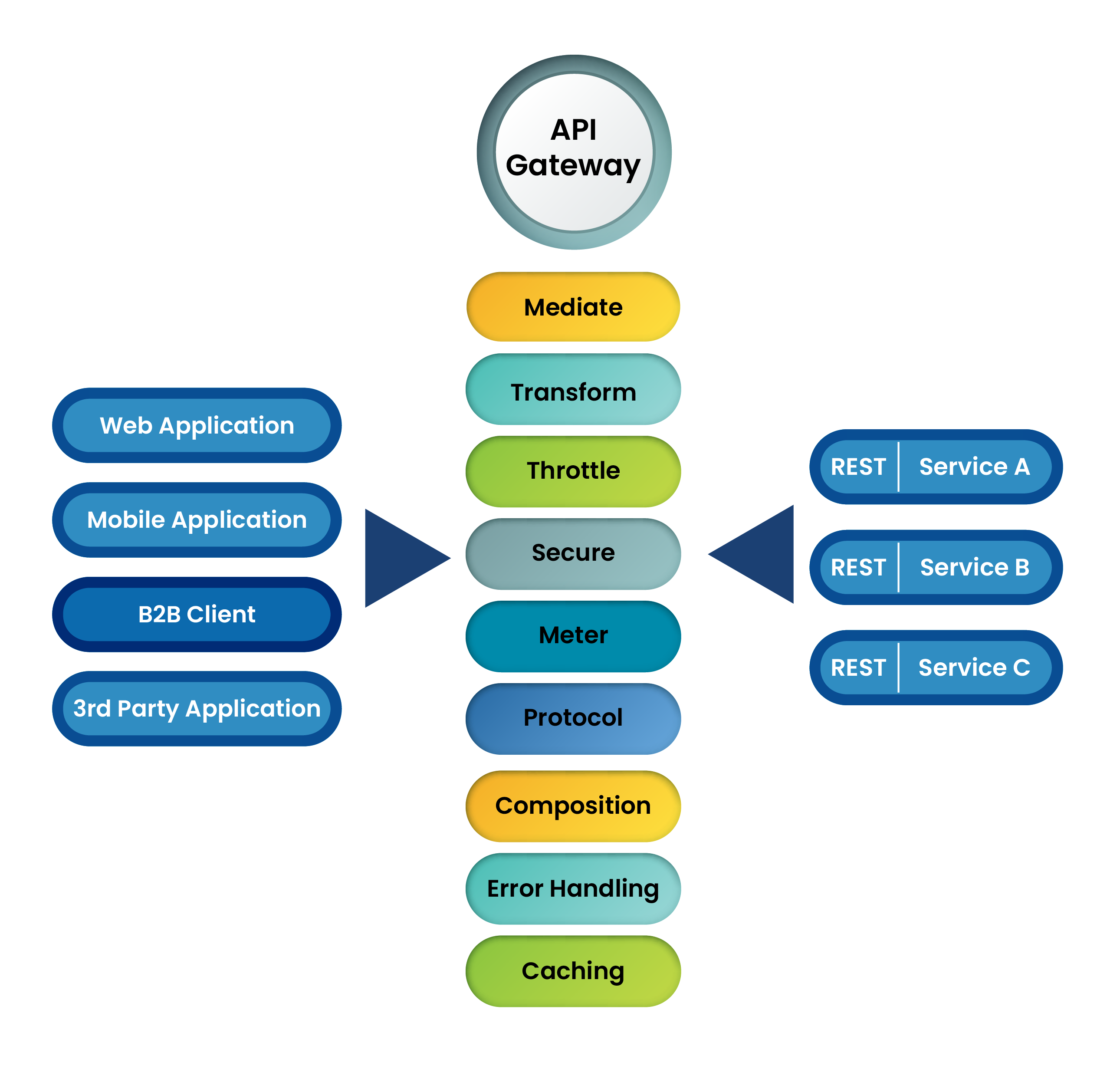
Business or Data Access Layer Common functional blocks of the business or data access layer include multi-purpose workflows, assignments, access lists, rules engine, integrations, audit trails, configurations, and data interfaces. In component architecture, such features are built as pluggable functionality. Similarly, for data interfaces, API design should factor areas like Authorization, Vendor Registration, Token management, Versioning, Service Quota, and Flow Orchestrations. API Gateways provide such functionality exceptionally well and can centrally manage data interfaces (APIs). |
 |
|
Data Layer With evolving requirements, new categories of databases like semi-structured and unstructured have also emerged. Along with traditional choices like Oracle, DB2, MySQL, PostgreSQL, there are also other database systems which can be considered, such as NoSQL (e.g., Mongo), columnar (e.g., BigQuery), Object oriented (e.g., Object- Store), Key-value (e.g., Redis), Document (e.g., CouchDB), Graph (e.g., Neo4j), Time Series (e.g., Influx) or Elastic Search databases. Choice of database depends on factors like read Vs write mix, distribution, integrity, concurrency, CAP, and the content. For example, key-value database is more optimized for user / password storage. |
|
|
Data Archival Certain standards, such as ISO27001, require applications to retain data for a given time period. Few standards also necessitate the audit trail capture of the changes. On the other hand, each data entity has a specific lifecycle and data loses relevancy over a period. Archival policy and data partitioning decisions may address such requirements and even offer query optimizations. For example, few bank portals enable historical statements only on request and such statements are retrieved from archived data achieved through horizontal partitioning. |
|
|
Personalization Applications offer layers of personalization ranging from user interface to the content based on user preferences or user attributes. Preferences / attributes work in tandem for UI experience and for personalized content retrieved from backend. Captured preferences may be managed at the server or the client end (mobile and web storage). Influencing factor, on the other hand, is used to determine if the same experience is present across all registered user devices Vs specific to each device or meet the middle ground. |
|
|
Media Handling Just as displays have different shapes and sizes, visual content is also captured in different pixel densities from LDPI to XXXHDPI. Videos follow resolutions ranging from 240p to 1080p. Vector images is another technique which uses points and paths, and can scale to any size without affecting the image quality. Applications either bundle the content within builds or externally store them with references. CDN networks, on the other hand, are more apt for static content where CDN providers maintain content replicas closest to the user geographical location for quick accessibility. |
|
|
DevOps With DevOps tools offering end-to-end development operations, present day tools are built to provide project management, sprint planning, code repositories and build pipelines services. Pipelines can accommodate test suites, code quality integrations, code deployment, and infrastructure provisioning through Infrastructure as a Code (IaaC). Other operational elements include parallel sprints, major / minor releases, backward compatibility,forward integration with new platforms, and publishing (to app store in case of mobile). Additionally, continuous evaluation and feedback loop improves operational efficiency. |
|
|
Testing Methodology There are various testing methods, such as, Behavioral Driven Development (BDD) for requirement behavior outcome, Test-Driven Development (TDD) for test coverage of coding (unit testing and automation tests), and Acceptance Test-Driven Development (ATDD) for acceptance test scenarios derived from the requirements. Some of the common front-end frameworks include Jasmine/ Karma, Mocha (Node), Jest (React Native), RSpec/Cucumber (TDD-Rails backend), PyTest and PHP Unit. It’s a good strategy to align coding and testing practices along with the overall quality and security. |
|
|
Code Quality and Security Testing Typically, applications are subjected to both black-box testing (DAST) and white-box testing (SAST) as they offer different coverages. SAST is used for early detection of coding practices and code quality, and DAST helps to get outside perspective on the application before go-live. Additionally, interactive application security testing (IAST) is used to analyze running applications, and runtime provisions for monitoring and protection. Based on the criticality of an application, the combination is chosen and is coupled with manual testing and automation testing on various device platforms and browsers. |
|
|
Application Security Security should be a design imperative since the initial stages of the application building as it drives several application build and deploy decisions. It starts with user authentication through various modes like SSO, LDAP, etc., moving to the next step of protecting the app in the hosting and deployment stage by enabling security headers (HSTS, CSP, X-Frame options, etc.). Third important step involves data encryption at rest and during transmission. Further, subjecting the infrastructure and application to VAPT testing reveals any security loops, and certifying against standards like OWASP 10 for web and mobile guarantees the required coverage. |
 |
|
Integrations Enterprise applications go through various integration scenarios and can leverage a range of options, such as, stateful vs stateless, transactional vs bulk, real-time vs near real-time vs batch, pull vs push, REST vs SOAP, SOA vs EDA pattern, JSON vs XML vs delimited formats and lastly, authentication through Oauth / JWT / basic. Integration design patterns illustrate various scenarios with examples and discuss entity maps, values maps, transformation, error handling, pre & post validations, and orchestration flows. When applications are refactored from monolith to microservice architecture, IPC channels or middleware (inter-process communication) are used for connecting services in pub-sub, SOA or in EDA architecture. |
|
|
Data Migration Migration planning should record and fulfil list of entities, data volume, data transformation, data cleansing, data dependency and data validation requirements. Defining unique keys, integration keys and relationship during data migration and following through ensures data referential integrity. ETL tools like Informatica, Talend, etc., facilitates most of the data migration requirements, including merge, de-duplication, lookup, transformation, error handling, and data reconciliation. |
|
|
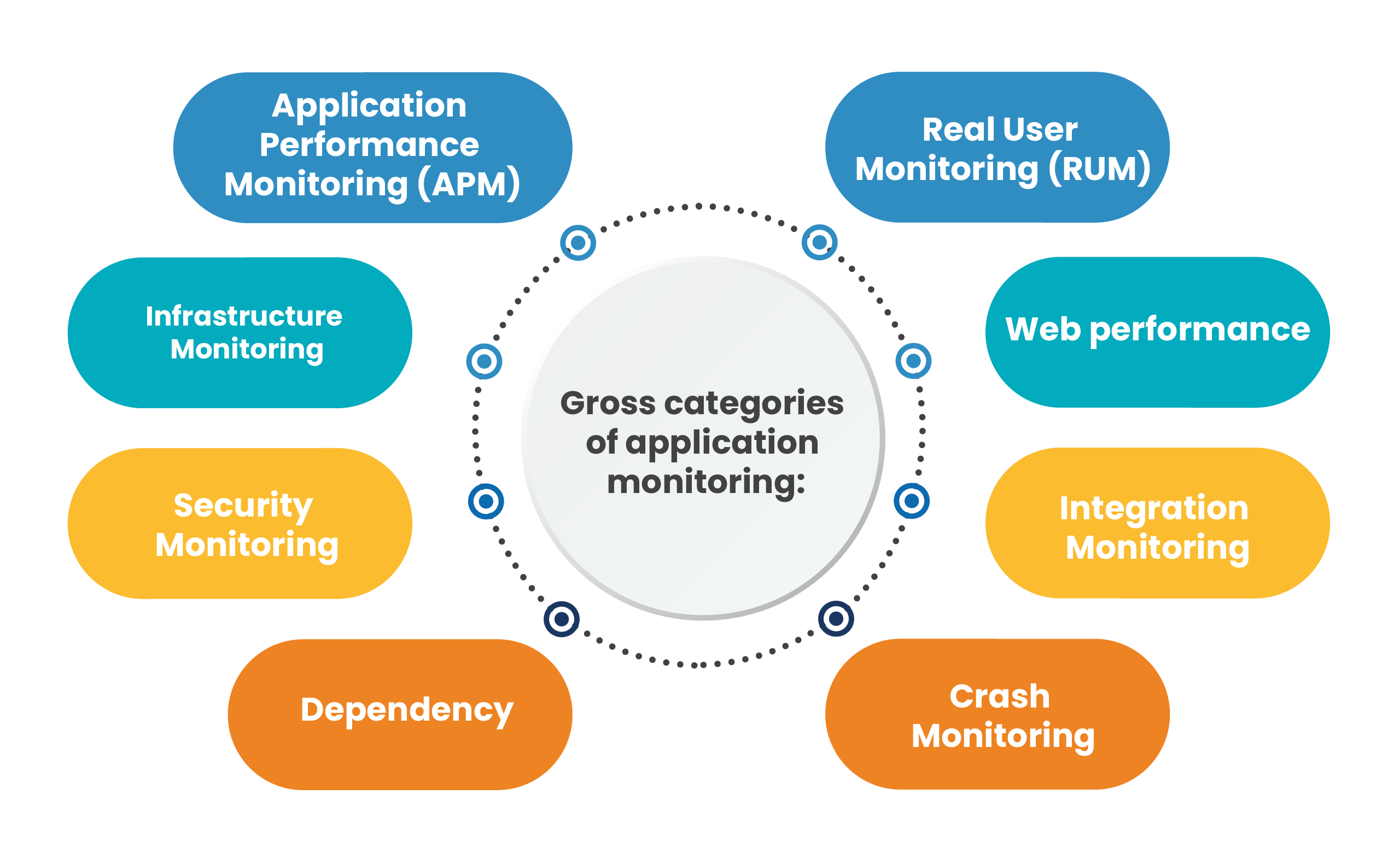
Application Monitoring For N-tier application, monitoring can be enabled at different layers and can span across multiple layers, for example, AppDynamics facilitates route trace from UI to database. Gross categories of application monitoring are Application Performance Monitoring (APM), Infrastructure Monitoring, Security Monitoring, Dependency, Real User Monitoring (RUM), Web performance, Integration Monitoring and Crash Monitoring. |
 |
|
Site Security Informational or eCommerce applications have different security requirements than a banking application. For internet facing application, certificate options available are Extended Validation Certificates (EV SSL), Organization Validated Certificates (OV SSL), Domain Validated Certificates (DV SSL), Wildcard SSL Certificates, Multi-Domain SSL Certificates, and Unified Communications Certificates (UCC). As per norms for each category of web application, compliant certificate through certifying authority (CA) is obtained and installed on server to adequately secure the HTTPS site. |
|
|
Tools Licensing Software tools are used at different stages of development and packaging of application. Usage and redistribution policies are usually overlooked due to ignorance or lack of interpretation. Legal department can help interpreting these clauses, as in few cases usage is only limited to education, non-profit sector or only for development. Few opensource licenses for reference are – Apache License 2.0, MIT, GNU GPL, LGPL, New BSD License, and more. Distribution, redistribution of binaries and copyright rules are to be followed equally for open source and other licensed products. |
|
|
Deployment Architecture Deployment choices for applications range from on-premises, private / public cloud, serverless (as service) to hybrid architectures, that leverage both on-premises and cloud components. Application components can be deployed together in a single system or across separate systems in distributed environments. With emergence of microservices, containerization of services, and distributed databases which are horizontally scalable, such dispersed deployment configurations are now commonplace. There are several cloud platforms such as AWS, Azure, GCP, IBM, Oracle, etc. and application platforms such as Oracle, GCP, Heroku, etc. which provide a range of development and hosting services. |
|
|
Administration There should be clearly defined roles for different stakeholders across all stages of the application building process. Enterprise applications are to be maintained for access, configuration, and content. User management is done by Administrators. Content, on the other hand, for specific module of application is maintained by module owner through Content Management System (CMS) portal. And accessibility to the application modules is compartmentalized and achieved through an access control list. |
|
|
Change Management Introduction of new application will bring change in terms of user experience, processes, and learnings. Publishing the benefits to stakeholders presents higher probability of seamless adoption. A change management process with trainings, pilots, hand holding, adding process champions, beta release, and higher management involvement turns out to be a success factor, and helps disseminate the change top-down and address any kind of stakeholders’ concerns. Additionally, continuous motivation and positive reinforcement usually add to the success probability. Apart from the list of factors to be considered mentioned above, there are a few other features like multi-lingual, multi-currency, multi-tenancy, notifications, analytics and machine learning which lead to design impact but are deliberately kept outside the scope. |
|
|
Use case of the application modelling To put things in perspective, let’s understand the usability of the various dimensions discussed here for modelling an enterprise application. The application being referred to is an already existing application snapshot running in the production and has considered every aspect of the application modelling discussed above. The application in context is a corporate employee engagement app which runs on web and mobile seamlessly. The App facilitates org-wide broadcasts categorically, including wall posts for peer connect, communities, events, chat, CEO connect for Q&A, help / assistance bot, and several other exciting features.
|
|
|
Conclusion With accelerated transformation and rapidly changing business models, there is an ever increasing risk of application building and deployment failures, leading to potential damage of business reputation and low customer satisfaction. Hence, provisioning against above dimensions from early stage of the application modelling will ensure that the enterprise application is secure, scalable, and resilient. A subset of these provisions will also be applicable for applications being migrated or refactored (using 7R model). At Microland, our digital strategy is based on a matured approach, covering all aspects of Cloud Platforms, Cloud Solutions, Cloud Migrations, Integrated Cloud Management (through Inhouse Products), Application and Cloud Observability (through Inhouse Product), DevOps enablement and information security (infosec secured ISO27001 certification), which are also the key factors in enabling a seamless, accelerated, and successful digital transformation journey for our customers. |
|
|
About the Author
Pritish Nandanwar, Senior Director - CIS, Microland. Pritish is an Enterprise Architect with 16 years of Industry experience in integration architecture, solution architecture, web application architecture, delivery methodologies, delivery pipelines, Micro Services and cloud solutions. |
|