Cybersecurity for Utilities Securing Critical National Infrastructure Environments

Cybersecurity attacks are growing rapidly in terms of frequency and sophistication. We are observing a whopping jump in cyber-attacks on critical national infrastructure (CNI) worldwide in recent times. CNIs are the lifeline of any country and are essential for the functioning of a society and economy.
Energy and Utilities which is one of the key CNIs has been undergoing digitalization which has made it prone to cyber-attacks such as denial of service, malware, and phishing. Moreover, cyber-attacks in the sector have caused significant disruptions to the entire network, including upstream, midstream, and downstream processes. Various types of cyber-attacks such as insider misuse, web application attacks, and physical risk/loss of property have affected the utilities industry. Several utility companies are reaching out to dependable and best-in-class technology providers who can protect their data, network, and resources from distinct types of attacks. Military alliances such as NATO are also considering classifying cyberattacks on the critical national infrastructure of member states as open declarations of war. We have witnessed threats such as BlackEnergy, Triton, and even the NotPetya and WannaCry ransomware outbreaks that had devastating effects on critical national infrastructure.
Geopolitical tensions also have an influence on cyberattacks. In March 2022, we observed that several alleged cyberattacks were perpetrated by different groups and state actors. It has now become critical to identify potential threats that may disrupt critical national infrastructures, especially in these times when geopolitical tensions are high.
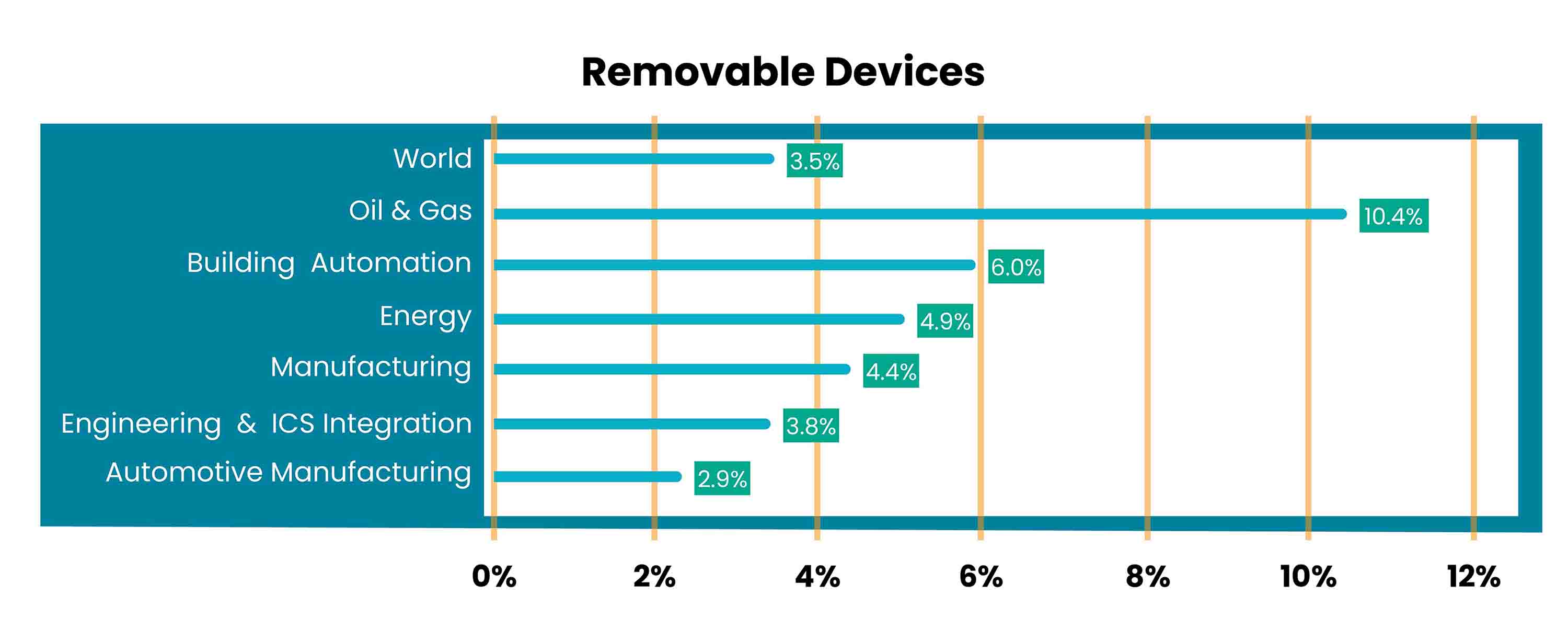
In the Oil and Gas industry, the percentage of Industrial Control Systems (ICS) computers on which threats were blocked when removable media was connected (10.4%) was 3 times the average percentage for the entire world (3.5%).[1]
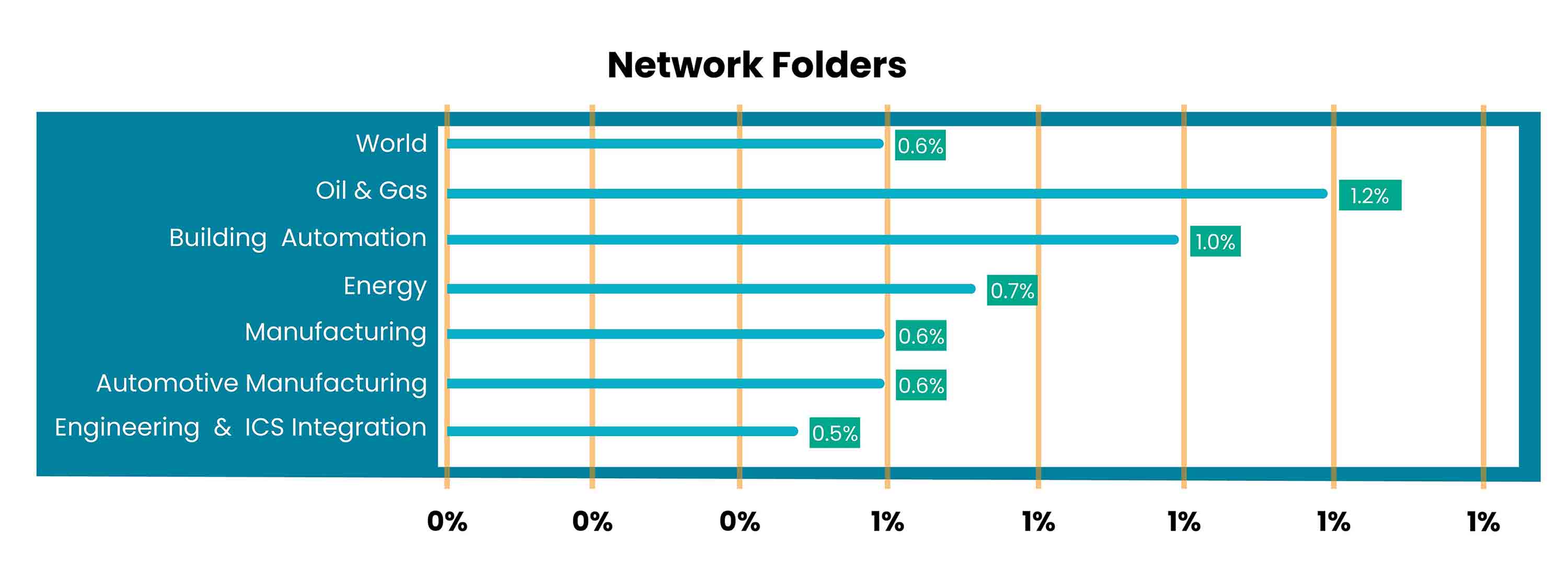
In the Oil and Gas industry, the percentage of ICS computers on which malware was blocked in network folders (1.2%) was twice the world average (0.6%).[1]
CISOs in the utilities space are more worried than ever before about cybersecurity threats. Half of them warn that their budgets are insufficient to cover the challenges that have emerged in recent times. As threat actors launch ever-more sophisticated attacks, CISOs are trying to position themselves as enablers of transformation. CISOs are acutely aware of the vulnerabilities their organizations face because of inflexible and insufficient budgets. On the other hand, maintaining compliance is the dire need of the hour.
As the cyber-physical world is becoming more digitized, Utilities companies have been compelled to adopt new operational processes and workflows to stay afloat. Right from web-enabled sensors that collect data to the adoption of cloud solutions, innovative strategies in the Utilities industry are transforming the landscape for operational technology (OT) environments. The current gamut of digital solutions integrates operational technology (OT) and information technology (IT) and leverage the power of emerging technologies such as AI and ML to enable Utility companies to innovate. The increased focus on digital transformation coupled with the need to unlock value from data to drive actionable insights is expected to grow steadily. This shift exposes critical national infrastructure, which is still in a quasi-traditional state, and entire utility supply chains to cyber risks making cybersecurity a core imperative for utility companies.
Cybersecurity in the Utilities industry needs to evolve to meet today’s security threat vectors. The speed at which technologies are evolving is arguably faster than ever, making it difficult to enforce security controls in real-time. When executing a solution strategy to secure OT cloud environments, security teams come across the following challenges:
- Expansion of Attack Surface: To catch up with the industry, Utilities companies are trying to embrace cloud technologies. However, to make it meaningful, they are also required to converge IT and OT networks which is broadening their overall cyberattack surface. In the past, OT systems remained on-premises, locked behind their corporate networks. Now, relatively insecure OT devices can introduce weaknesses in the organization’s cloud infrastructure or vice-versa.
- Misconfigurations in the Cloud Estate: Building on the broadened attack surface, misconfigured cloud resources leave critical OT environments at risk. Malicious actors target such misconfigurations and move laterally within the OT infrastructure which can have catastrophic consequences. With cyber and physical systems now interconnected, utility companies risk physical harm to employees and data exfiltration.
- Vulnerability to Legacy Systems: Industrial Control Systems (ICS) have been at the heart of OT cyber-physical infrastructure. However, the idea of connecting ICS to the cloud is relatively new. Exposing such traditional systems to the cloud can potentially introduce a range of vulnerabilities to critical infrastructure which is less resilient than its interconnected IT system. This makes Utilities companies a sitting duck for cybercriminals to leverage historical tradecraft to gain access and perform reconnaissance before employing more sophisticated techniques once they have exploited the vulnerabilities of their target.
In our endeavor to build an adaptive cloud security strategy for the Utilities industry, we strongly recommend organizations to weave security into their overall technology transformation charter as they build out their roadmap for new hybrid infrastructure deployments. We employ best practices for managing OT and cybersecurity by design which includes:
- Adherence to global security standards: Building a cloud infrastructure that aligns with security standards like IEC62443 and NIST framework
- Centralized security monitoring: Centralizing asset and traffic visibility and monitoring across the IT and OT environments
- Application security: Tracking and reporting on software vulnerabilities in OT and IT space
- Platform security: Deploying security controls as part of the foundation rather than as an afterthought
Microland’s strategy is to ensure security across on-premises, cloud, and hybrid infrastructures using an adaptive approach. We proactively ensure:
- Solution hardening: Reducing the vulnerability of the solutions, including risk assessment, threat and vulnerability detection, and port management
- Network Security: Supporting segmentation and management of networks across IT and OT estate.
- User Security: Support for managing operating systems and user account security (authentication and authorization) across the environment
- Application security: Deploying security control to monitor applications
- SOC monitoring using Security Information and Event Management (SIEM): Management of security-related information and events, generally for security incident handling and forensics.
- Patch Management: Validation and installation of security patches
- Backup and restore: Backup and restore the functionality of the automation solution and its products
Microland helps orchestrate all these security solution components to ensure safe, sustained operations which is top priority for leaders in the utilities sector. There is no doubt that many CISOs have risen to the challenge and can today demonstrate the growing strategic importance of their role. Notwithstanding, it would also be fair to highlight that the crisis in the utilities sector has exposed weaknesses in cybersecurity. It is imperative for CISOs to accelerate their efforts to address security by design and actively participate in strategic infrastructure and technology investments.
References
Threat landscape for industrial automation systems for H1 2022
Read More