Cybersecurity Mesh Architecture: A metamorphosis impacting the cyber world

Current State of Affair
Be it Sony or Colonial Pipeline attack, various organizations have got caught like a sitting duck at the mercy of attackers. Even after paying the ransom, some of them could never recover and had to file for bankruptcy. Ransomware and other cybersecurity attacks feature in the news almost on a daily basis. It has become a lucrative revenue stream and a potential for sabotage in some cases for malicious actors. Cybercrime (especially ransomware) has led to serious disruptions, particularly when it targets critical infrastructure.
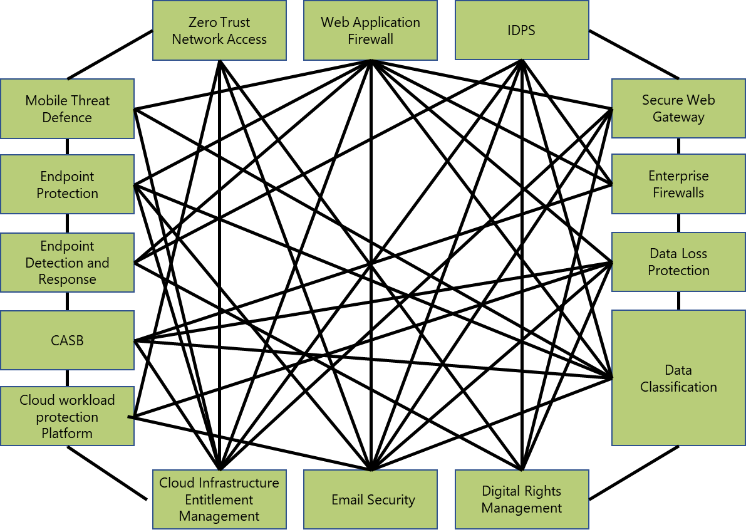
The reality is that the attackers don’t think in silos, whereas organizations often deploy pointed and siloed security solutions. Hackers usually engage in lateral movement which involves targeting weakness in one area to exploit the adjacent area. Further, with digitalization, the perimeter has become more fragmented, and to tackle this, many organizations are adopting a multi-cloud strategy. The data is no longer residing in the company-owned data centers, and users are able to access cloud-based applications from anywhere. Within a distributed environment that supports assets everywhere and access from anywhere, identity and context have become the ultimate control surface. However, the multi-cloud adoption has posed another challenge as every cloud provider supports a different set of policies, and hence creating a consistent security posture across cloud providers becomes challenging. This has led to a security sprawl that complicates management, fragments visibility, and limits the ability of an organization to respond to threats effectively.
What is needed to address the current cybersecurity challenges?
Gartner recommends a change in the way we look at addressing cybersecurity challenges today. In the current technology landscape, enterprises need a complete paradigm shift, something beyond the OpenXDR approach but on similar lines. The new approach will help to:
- Evolve your security infrastructure to be more integrated, focusing on centralized administration and policy enforcement
- Choose cybersecurity solutions which provide integration flexibility via plug-in APIs that allow extensions and customization, standards support, and extensible analytics
- Close interoperability gaps between different vendors’ solutions by using current and emerging security standards
While in principle this is the requirement, it’s difficult to implement and manage this in reality. Soon the mesh may turn out to be a mess!
Hence, there was need for a reference architecture to abstract this thought and bring in manageability in the approach. The underlying framework suggested by Gartner is Cybersecurity Mesh Architecture (CSMA).
Benefits of Cybersecurity Mesh Architecture (CSMA)
Cybersecurity mesh architecture provides a foundational support layer that enables distinct security services to work together to create a dynamic security environment. CSMA provides a more consistent security posture to support increased agility for the composable enterprise. As organizations continue to invest in new technology to enable digitalization, CSMA provides a flexible and scalable security foundation that provides bolt-on security for assets in hybrid and multi-cloud environments. CSMA also creates a better defensive posture through a collaborative approach between integrated security tools with detective and predictive analytics. The outcome is enhanced responsiveness to breaches and attacks. Cybersecurity technology delivered through this model takes less time to deploy and maintain while minimizing the potential for security dead ends that cannot support future needs. This frees cybersecurity teams for more value-added activities.
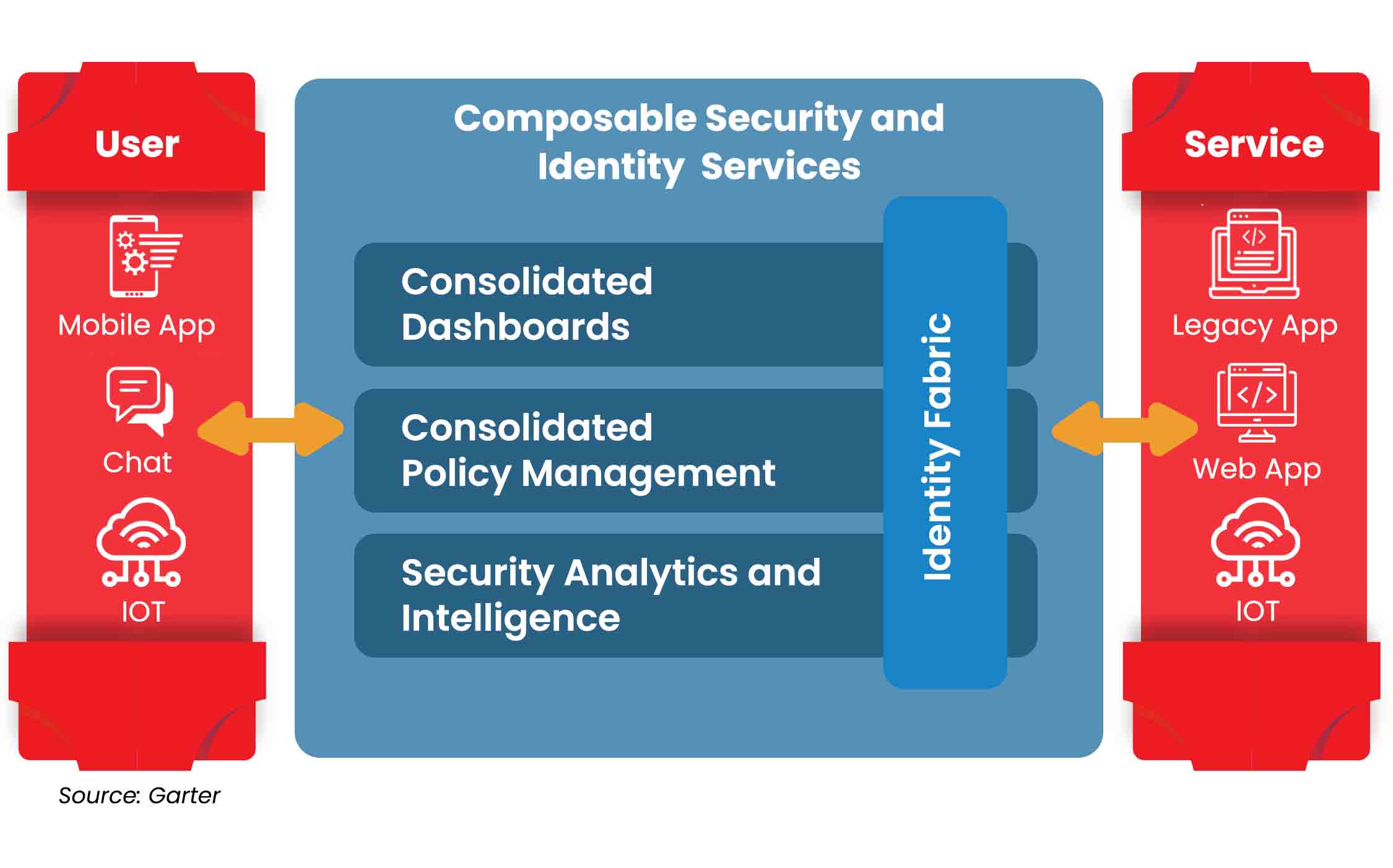
Cybersecurity Mesh reference architecture brings in multiple foundational layers which act as a force multiplier when integrating different security products. The architecture focuses on composability and scalability by extending security controls to widely distributed assets. Rather than every security tool running in a silo, a cybersecurity mesh enables tools to interoperate through several supportive layers, such as consolidated policy management, security intelligence and identity fabric.
CSMA fosters a more consistent security posture to support increased agility for the composable enterprise. It provides a foundation for entities (people, processes, things) to connect securely from multiple locations across hybrid and multi-cloud environments, channels, and diverse generations of applications, protecting all the organization’s digital assets.
CSMA intends to bring in composability, scalability, and interoperability for security controls through the following four foundational layers:
- Security analytics and intelligence: To combine data and lessons from other security tools, and provide analyses of threats and trigger appropriate responses. The two main components to empower this are the Security data lake and AI. It fuses and correlates data (logs and telemetries) from all the security tools and shares it back.
- Distributed identity fabric: To provide capabilities such as directory services, adaptive access, decentralized identity management, identity proofing, and entitlement management. This includes:
- A unified approach for IAM, covering all types of identities and access to all types of services, across all areas of IAM. It’s a paradigm for comprehensive and future-proof IAM that can be implemented based on existing or new technologies
- Built on APIs and microservices
- Consolidated policy and posture management: To translate a central policy into the native configuration constructs of individual security tools or, as a more advanced alternative, provide dynamic runtime authorization services. It calls for a high level of interoperability and a control plane that manages and translates policies into the native format. This is the biggest area which needs a lot of work to be done and a standard to be arrived at.
- Consolidated dashboards: To offers a composite view into the security ecosystem, enabling security teams to respond more quickly and more effectively to security events. It gives CISOs a comprehensive view of cybersecurity posture of the organization.
Enablers of the CSMA implementation
The key enablers to implementing the CSMA are:
- A single-pass cloud-delivered solution which securely and intelligently connects things, processes, and people
- Everything as a service
- Software-defined
- API based
- Comprehensive access governance
- High-speed communication channel to provide faster response time with enhanced security and privacy capability to deliver high availability, reliability, and scalability
- Security data lake and (responsible) AI to deliver Analytics, Visibility, Automation, and Orchestration, making cyber-response precise, automatic, faster and simplified
Microland’s Readiness for CSMA
Microland has been recognized by various analysts’ groups for its offerings and expertise in Network and Cybersecurity space. Microland has been identified as a leader in Gartner’s Magic Quadrant for Network managed services.
It has a rich vendor ecosystem to support its journey and enablement on CSMA. Microland is well-placed in terms of its offerings on SASE, SDWAN, Zero Trust, IAMaaS, ADR, Cloud security services, and MicroShield (Microland’s internal IP to provide a persona based single pane of glass) which are the building blocks of CSMA.
References:
https://securityintelligence.com/articles/cloud-security-trends-cybersecurity-mesh/